What would happen if someone had access to all your data? How secure are your web accounts? Are you concerned about cybersecurity? You should be!
With data breaches and cyberattacks becoming more frequent, maintaining good cyber hygiene is as crucial as protecting your banking and personal information.
An example of a huge data breach was the Facebook-Cambridge Analytica scandal, where the latter hired a researcher to create an app that collected private info from Facebook users and their friends without their consent. The data was used to target political ads for the 2016 US presidential election and the Brexit referendum.
Financially speaking, the firm Cybersecurity Ventures reported that the global cost of cybercrime is predicted to be a staggering $10.5 trillion annually by 2025. Meaning that e-crime could account for over 10% of the world’s GDP.
The following 11 smart tips will help you build your digital fortress with walls of encryption and moats of security protocols to keep enemies at bay. They’re not that difficult to implement.
Today’s Focus of Attention is reader-supported. We sometimes include products we think are useful for our readers. If you buy through links on this page, we may earn a small commission.
Create Strong Passwords: The Stout Locks

This is the first line of defence. Skip easy-to-guess passwords like ‘qwerty’, or your birthdate.
According to a study by the UK’s National Cyber Security Centre (NCSC), millions of people are still using weak passwords such as ‘password123’ on sensitive accounts. Instead, opt for a mix of letters, numbers, and special characters.
Mac OS, for instance, gives you options when creating new secret codes, which are then stored in iCloud.
Also, to boost virtual security levels, change your passwords regularly and use different ones for different platforms.
Each online service is a potential gateway for cybercriminals to access your personal or professional information. So, having the same password across multiple platforms is akin to using one key to unlock every door in your house. Once a hacker has it, nothing is safe.
Cultivate the habit of changing passwords to ensure a robust digital safety posture.
Enable Multi-Factor Authentication (MFA)
Why settle for one layer of security when you could have more? Multi-factor authentication requires additional forms of identification to access resources and data. As with passkeys.
This system is more secure since the user has to provide another piece of information apart from the username and passcode. With this strategy, hackers find it harder to reach your info, even if they have stolen or guessed the code.
Three different factors are used, along with an account password, during MFA:
1- PINs, passphrases, and security questions like “What was the name of your first pet?”
2- Hardware: smartphones, hard or soft tokens, key fobs, and smart cards. You can insert a smart card into a device, receive a one-time passcode (OTP) via SMS, or generate a unique code using a physical token to verify your identity.
3- Biometrics, such as fingerprint or retinal scans, voice, or facial recognition.

Let’s say you log in to your email account. After entering your login credentials, you might need to enter a short-lived code that is sent through SMS or an app. Thus, if someone else tries to sign in but doesn’t have your phone, they will not have access.
A notable example is Google. It asks for the usual password and can send a passcode to your mobile via SMS, voice call, or through Google Authenticator.
If you’ve enabled MFA on any of your accounts, let your network know this smart move.
Protect Against Invisible Invaders

Outdated software is like a rusting shield. Make sure your operating system – Mac, Windows, iOS, or Android – is up-to-date.
The latest security patches safeguard your OS against attacks from malicious individuals who want to gain access to credit card numbers, passwords, and personal data. Additionally, ensure your firewall software is also updated, enhancing your device’s ability to fend off evil assaults.
In May 2017, more than 200,000 computers running outdated Windows systems were victims of a global cyberattack. The criminals used a stolen NSA software called EternalBlue to remotely encrypt the victim’s files and demand ransom in Bitcoin.
Hackers exploit your outdated device, stealing information and posing as you, using your email address and phone number to send messages, seek money, or buy things on Amazon or eBay.
But the worst scenario is that they might sell your digital content to kidnappers and blackmailers.
Stay Away from Public Wi-Fi
Public networks are the breeding ground for potential risks. There, hackers may inject trojans into your phone or laptop, and see who you’re chatting with, what operations are running, and even to whom you send emails.
A survey by NordVPN found that one in four people have been hacked while using public Wi-Fi abroad in restaurants and hotels. While the FBI reported almost 800,000 complaints of suspected internet crimes, most of them involved the use of public networks.
Free wireless internet is convenient in places where the signal is weak or non-existent, or because you don’t have enough data, but it’s of high risk.

Opt for a larger plan for your mobile if you are a heavy byte eater while on the go. It’ll be more expensive, but safer. But if you have no choice, connect to a public Wi-Fi only through a Virtual Private Network.
Use a Virtual Private Network (VPN)

Navigating the internet without a VPN is like sailing in shark-infested waters with no cage.
When you go online, your device sends and receives data via an internet service provider. So, the ISP is able to track any digital operations, browsing history, and even sell your preferences to advertisers. That’s why you receive hundreds of emails in your inbox every day.
A VPN works like Harry Potter’s cloak of invisibility for your files, protecting them from hackers and governments without being decoded or intercepted.
With a VPN, your data is first encrypted on your device and then sent to a server based in a different location, where it’s decrypted and directed to its destination on the web. Some trusted VPN providers on the market are NordVPN, Express VPN, Surfshark, and Private Internet Access.
Read this article about VPNs we published a few weeks ago. Spread the word about safe browsing.
Check Your Web Security
Sharing personal details on an unsecured site is akin to leaving your wallet in a room full of strangers.
Before entering any confidential information on a website, look for ‘https://’ in the URL and a padlock symbol in the address bar. It shows that the webpage uses SSL (Secure Socket Layer) encryption.
Unlike HTTP, HTTPS encrypts the data between your computer and the server, making it tough for hackers to eavesdrop on the communication.
To illustrate, if you are shopping online and enter your credit card numbers on an HTTP site, a hacker could intercept this info. However, on an HTTPS page, your banking details are encrypted.
One well-known case where user data was taken from an HTTP site is the Equifax data breach. In September 2017, the company announced that hackers had accessed its system and stolen information of about 147 million people, including names, social security numbers, birth dates, addresses, and credit card numbers.

While the best is to avoid HTTP sites, not all are dangerous. It might be okay to read news on an HTTP site since you’re not required to enter any digital footprint. But, for banks, online shopping, or subscriptions, make sure that the website is an HTTPS one.
Be Cautious with Social Media

Have you seen crime TV shows where people share private information on social media? Typical results are invasion of privacy, identity theft, blackmail, defamation, harassment, or even violence. Make sure you’re not throwing open the curtains for all to see.
In 2019, an Australian woman was stalked by a man who used her Instagram posts to track her down, following her to a cafe, train station, and her house.
Another case was in California, when a couple posted pictures of their holiday on Facebook. After watching the images, thieves broke into their home and stole jewellery, cash, and electronics.
Also, a man in the US was arrested for identity theft after he got personal details from Meta and LinkedIn. He used the stolen identities to open accounts with various banks and retailers, racking up over $100,000 in fraudulent charges.
55% of teens have given out confidential details to strangers, including photos and physical descriptions. Sexual assault cases linked to virtual communities have tripled, with 29% starting on a social networking site.
You have no idea how dangerous it is.
Statista found that 53% of internet visitors worldwide were more concerned about their digital security than they were a year ago, with the highest levels of concern being Latin America (75%), the Middle East, and Africa (65%).
29% of people on online platforms have experienced stalking, and 66% of adult Facebook users are unaware of the platform’s protection settings. And these figures are constantly growing as more subscribers join social media.
So be mindful of what you share. Even seemingly innocent information may be used against you.
Use Incognito Mode (it helps, sometimes)
This mode does not save your history, temporary cache, cookies, passwords, autofill, or site permissions on your computer. They are cleared once you leave the incognito windows.
However, it doesn’t mean that others can’t see you; they can. It’s only a measure to avoid saving files from external sources, but not a substitute for other security measures.

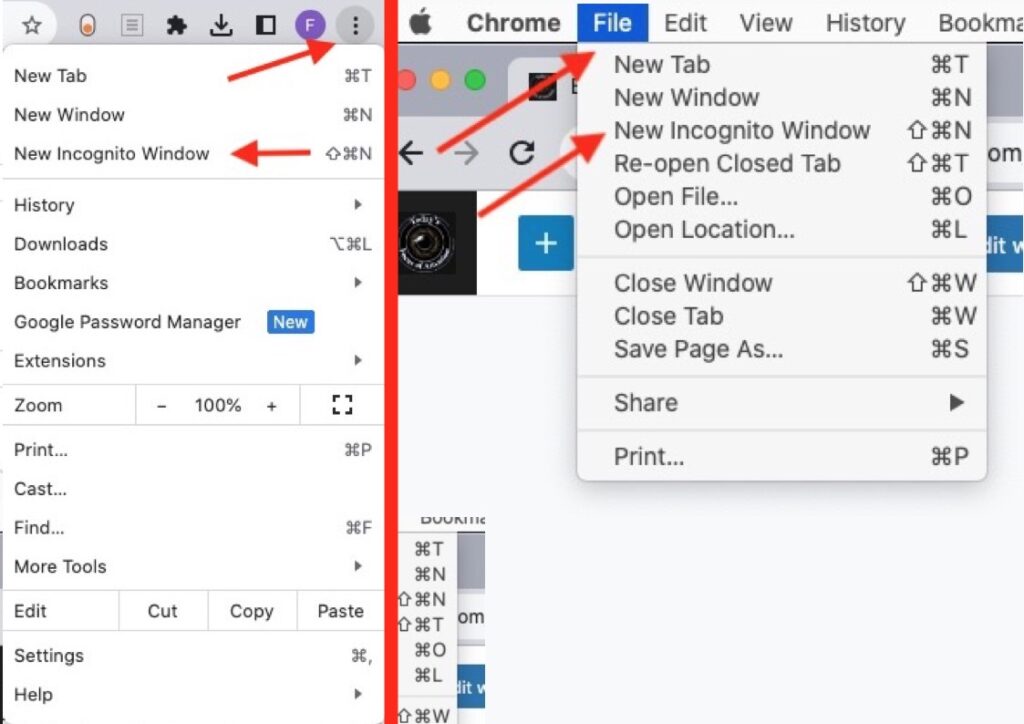
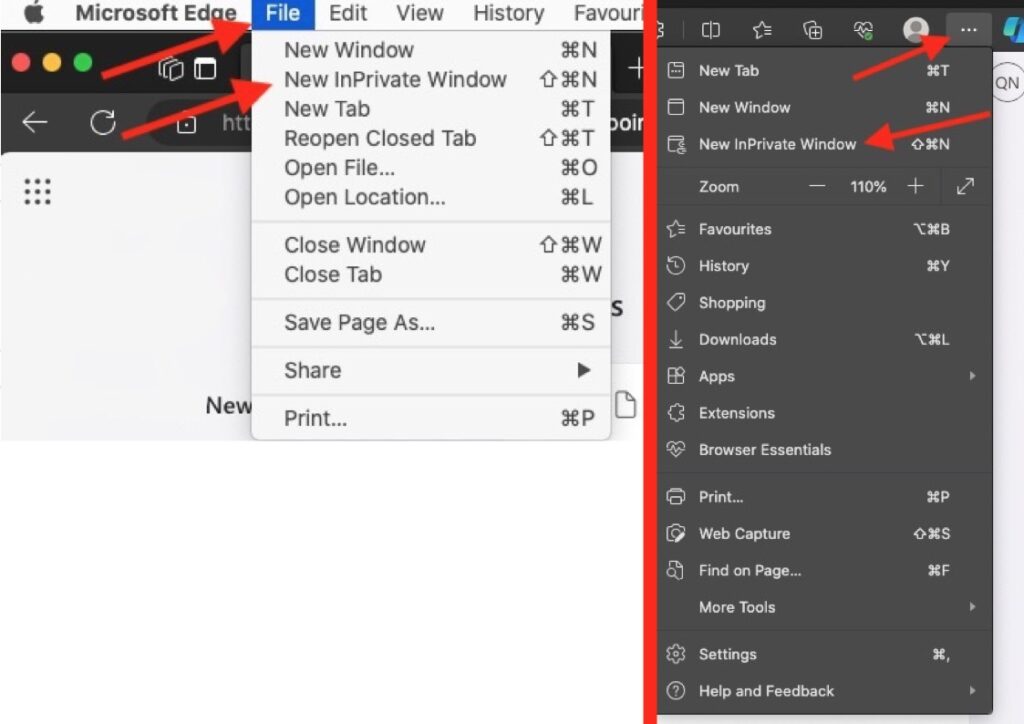
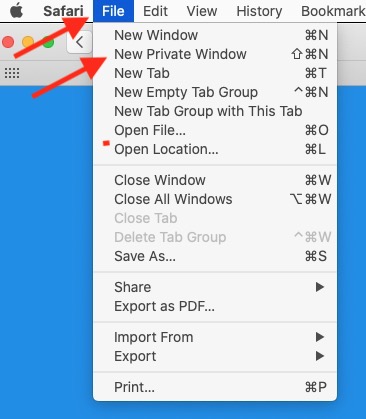
How to Activate Incognito Mode in Different Web Browsers
Click on the three dots icon on the top right corner of your window and pick ‘New Incognito Window’ or in ‘File – New Incognito Window.’
Go to ‘File’ and select ‘New InPrivate Window’ or choose ‘Settings and more’ (the three dots icon) in the upper right corner of your window and press on ‘New InPrivate Window.’
Be Sceptical of Suspicious Emails and Links

From the avalanche of electronic mail you receive every day from unfamiliar accounts, websites, and stores, most are email phishing. They are wolves in sheep’s clothing.
Phishing is a scam where criminals send fake emails to trick people into sharing personal information like passwords and credit card numbers.
Be very careful when clicking on links or opening attachments, especially from unknown contacts. They could contain malware that, once implanted into your computer, can get sensitive data from your device.
Common signs of phishing scams include unexpected emails urging immediate action, such as updating your account details or verifying your identity, often accompanied by a threat of suspension. Also, the email may come from an unrecognised sender with a domain that is a slight misspelling of a legitimate website name.
A famous case was the Google Docs Phishing Scam in 2017. It involved fake emails that appeared to come from contacts of the victim, inviting them to view a Google Doc. Once open, the file released a malicious app that could read emails.
Be alert for generic greetings like “Dear Customer” as opposed to personalised ones and poorly written emails with spelling and grammar mistakes. If an email instils a sense of panic or urgency, verify its authenticity by contacting the company through official channels rather than replying to the suspicious message.
Secure Your Mobile Phone
Your smartphone has a wealth of personal information, such as banking passwords, contacts, and business documents. Would you leave it open for anyone to read?
This year, a woman in Singapore received a call from someone claiming to be from the Ministry of Health who asked her to download an app to verify her vaccination status. The app turned out to be malware that gave the scammer access to her phone and bank accounts. It resulted in the woman losing $12,000.
In 2022, a man in the US was tricked into installing malicious software that pretended to be a Covid-19 contact tracing app. This malware recorded his audio and video conversations, tracked his location, and stole his personal data.
In the UK, a couple received a text message from their bank, asking them to confirm a suspicious transaction. The SMS contained a link that directed them to a fake website that look identical to their bank’s site. The couple then entered their log-in details and private codes and lost £20,000.

Always use biometric security features such as fingerprints or face recognition to access banks or online shopping apps. And remember to keep your device’s OS up-to-date.
Often Review Account Settings: The Locks on Your Doors and Windows.
Take your time to check the privacy settings on your online accounts. You may not know that someone else is watching every move you make.
For social media platforms (Facebook, X, Instagram), verify that you are sharing your posts with the intended audience.
Furthermore, activate login alerts to be notified of unauthorised access attempts.
Regarding emailing (Gmail, Outlook), review recent sign-in activity, account recovery options, and authorised third-party applications. At the same time, check for forwarding addresses or filters.
When it comes to banking and financial platforms, turn on notifications for transactions and access attempts, and activate multi-factor authentication.
Update passwords and manage the list of devices for your account.
Similar to banking, for online marketplaces (Amazon, eBay) search connected gadgets, enable 2FA, if available, and refresh log-in codes regularly. Don’t forget to confirm your shipping address and payment methods on a regular basis.
In cloud storage services (Dropbox, OneDrive, Google Drive) check who is able to use your stored files and folders, allow two-factor authentication, account recovery options, and authorised gadgets.
With subscriptions like Netflix or Spotify, review and update payment info as well as the devices connected. Ensure only trusted individuals connect and check your profile activity.
Online privacy is not something to be taken lightly. Be aware of what could happen if you let a cybercriminal learn about your life, finances, and preferences.
With these smart tips, you’ll be well on your way to creating your digital fortress to protect your personal information from attackers. Be the vigilant guard at the gates of your virtual kingdom. Do you have any other recommendations to stay away from online threats? Please share your thoughts.



2 thoughts on “11 Essential Tips for Ensuring Online Privacy – Build Your Digital Fortress”